NAME
lsblk - list block devices
lsblk lists information about all available or the specified block devices. The lsblk command reads the sysfs filesystem to gather information. The command prints all block devices (except RAM disks) in a tree-like format by default
[root@nsk postfix]# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 20G 0 disk
├─sda1 8:1 0 1G 0 part /boot
└─sda2 8:2 0 19G 0 part
├─centos-root 253:0 0 17G 0 lvm /
└─centos-swap 253:1 0 2G 0 lvm [SWAP]
sr0 11:0 1 1024M 0 rom
The default output, as well as the default output from options like --fs and --topology, is subject to change.
[root@nsk postfix]# lsblk --fs
NAME FSTYPE LABEL UUID MOUNTPOINT
sda
├─sda1 xfs 7b4cffc6-3fe2-4ad9-9be9-ea83e11532fc /boot
└─sda2 LVM2_member DQjmHN-fso4-Mu4t-3l1V-Yogj-ksTH-ROFiK7
├─centos-root xfs 4d056c54-3e98-4bbd-953d-ad49d24e89a3 /
└─centos-swap swap e97f5f2c-66b2-42c6-9baf-544123ee9abf [SWAP]
sr0
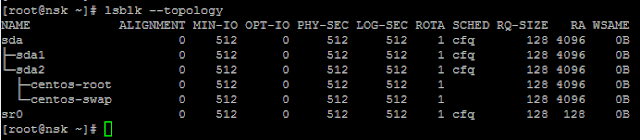
[root@nsk postfix]# lsblk --topology
For mre help, please refer man pages
lsblk - list block devices
lsblk lists information about all available or the specified block devices. The lsblk command reads the sysfs filesystem to gather information. The command prints all block devices (except RAM disks) in a tree-like format by default
[root@nsk postfix]# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 20G 0 disk
├─sda1 8:1 0 1G 0 part /boot
└─sda2 8:2 0 19G 0 part
├─centos-root 253:0 0 17G 0 lvm /
└─centos-swap 253:1 0 2G 0 lvm [SWAP]
sr0 11:0 1 1024M 0 rom
The default output, as well as the default output from options like --fs and --topology, is subject to change.
[root@nsk postfix]# lsblk --fs
NAME FSTYPE LABEL UUID MOUNTPOINT
sda
├─sda1 xfs 7b4cffc6-3fe2-4ad9-9be9-ea83e11532fc /boot
└─sda2 LVM2_member DQjmHN-fso4-Mu4t-3l1V-Yogj-ksTH-ROFiK7
├─centos-root xfs 4d056c54-3e98-4bbd-953d-ad49d24e89a3 /
└─centos-swap swap e97f5f2c-66b2-42c6-9baf-544123ee9abf [SWAP]
sr0
[root@nsk postfix]# lsblk --topology
For mre help, please refer man pages