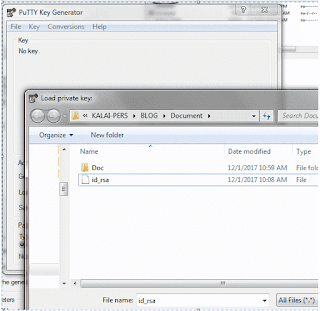
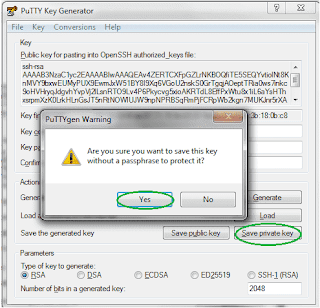
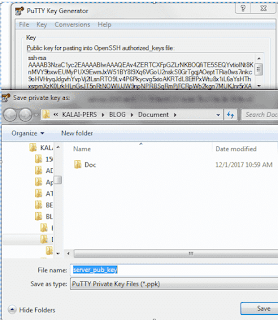
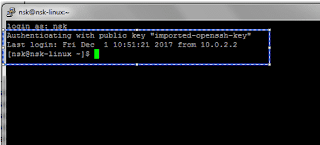
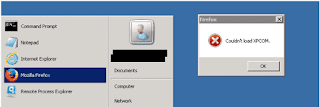
Situation:
Solution:
Restart nslcd service.
[root@testserver~]# /etc/init.d/nslcd restart
Stopping nslcd: [ OK ]
Starting nslcd: [ OK ]
NAME
nslcd - local LDAP name service daemon. nslcd is a daemon that will do LDAP queries for local processes based on a simple configuration file.
Openldap user is having issue while login to the server, it is asking password again and again.
Solution:
Restart nslcd service.
[root@testserver~]# /etc/init.d/nslcd restart
Stopping nslcd: [ OK ]
Starting nslcd: [ OK ]
NAME
nslcd - local LDAP name service daemon. nslcd is a daemon that will do LDAP queries for local processes based on a simple configuration file.